
Info
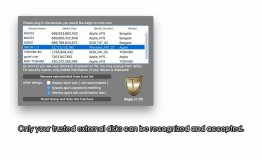
Protect your Mac against threats from external drives, whether Thunder, Firewire, USB disks or flash drives, or even SD cards! → Insert a flash drive and copy, this is the most common way your confidential documents or files are stolen, even in the modern era of cloud storage. One of our other apps called “plugSHIELD” is a great protector if your Mac is in a public place: As soon as your Mac is plugged in, it prevents any storage devices from trying to access your Mac. log that storage device for you so you can find the culprit. But what if your Mac is for personal use and you want to make exceptions for your Time Machine backup disk, portable external drives, SD cards in your camera, or the flash drive in your keychain? Try Aegis! While you will block all storage devices that are NOT on your preset whitelist, those on the list will automatically be granted free access. You can even choose which partition on a physical hard drive is mounted and which is not! Adding a device to your whitelist is simple: Open Aegis' preference interface, plug in the device, and then unplug it without even a single mouse click – it's that simple. Removing a device from the whitelist is also extremely simple, just select the disk and click the delete button. → And to make it even cooler, Aegis can even block or unblock individual partitions of a storage device! To make your Mac truly secure, Aegis itself is password protected and your whitelist is saved in data mode to prevent it from being modified. Aegis also retrieves as much information and parameters as possible from your disk, so no clone can fool it. And unlike similar apps, Aegis will not write anything to your devices. → Aegis is your Mac's faithful protector against spies and malware.
Features
- Prevents any unauthorized external storage device from accessing macOS
- Gives you additional flexibility by blocking even individual partitions of a single disk.
- Does not delay any devices on the whitelist when plugged in.
- It will not issue an error message when blocking a device, thereby confusing any potential intruder who would probably check out their device instead.
- It is password protected and cannot be broken out.
- The user's trust list is properly recorded to prevent compromise
- Can detect and reject cloned devices.
- Does not save data, pointers or files on any of your devices.
- Adding devices to the trusted list is simple, no keystrokes or mouse clicks required!
- Dock icon can be hidden (highly recommended and already set by default)
System Requirements
Compatibility: macOS 11.0 or later • Apple Silicon or Intel Core processor
Screenshots
Download Links
Turbobit 4 MB .dmg



























Add Comment